- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US
- …
- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US


- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US
- …
- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US

Security By Design
Building security into your products, processes and service from the ground up.
Security / Protection Profile
Our specialized experts helps you plan and build the right security for your ICT/IoT product. From a broad Security Profile to a detailed Protection Profile and a tailored Security Target, we guide you every step of the way.
- 🛡️ From Chip to Cloud, we create a tailored, risk-based set of requirements for your IoT products or solution
- 🔒 Define requirements, choose security solutions, and save time with our experienced approach, adapting to consumer, enterprise, industrial, and critical environments.
- 🎯 Achieve economical security assessment, focusing where risks are highest.

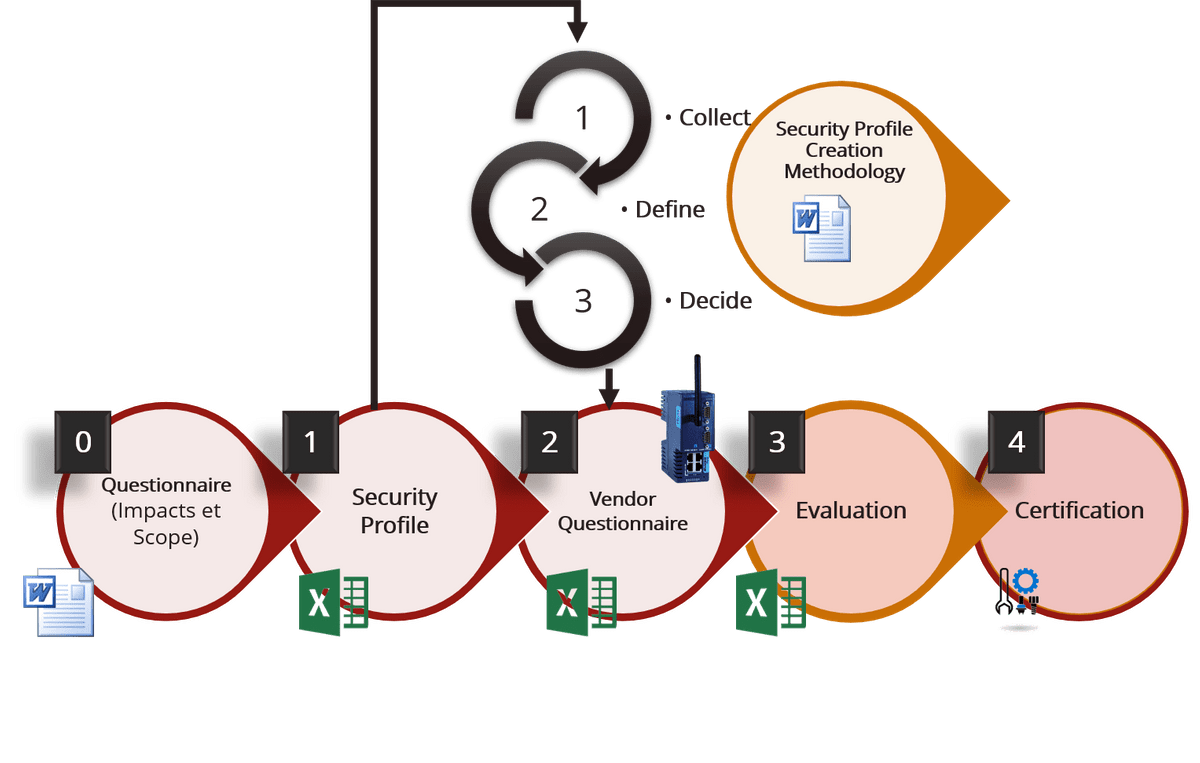
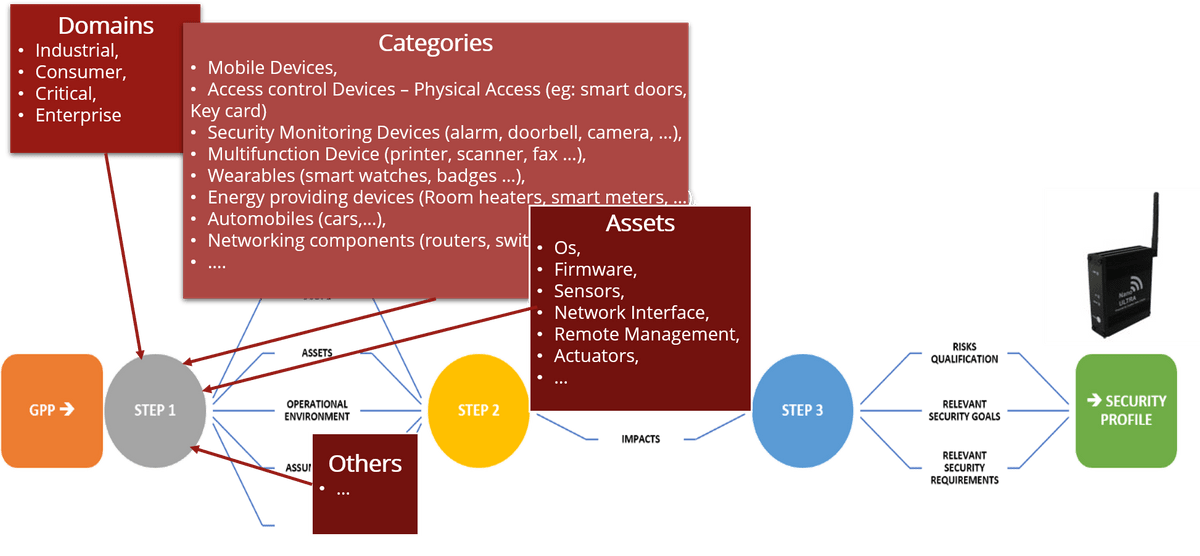
Security Profile (SP) - Your Security Blueprint
Imagine your IoT product - whether it's a smart camera, mobile phone, thermostat, or an industrial machine - as a house. Now, before you build that house, you need a blueprint that shows where everything should go to make it safe and secure.
A Security Profile is like that blueprint for your product's security. It lists out all the security requirements tailored to what your product is and how it'll be used. This way, you can focus your efforts where the risks are highest, helping you save time and money.

Protection Profile (PP) - The Generic Security Standard
You want to make sure your house (product) is up to standard, but what standards should you follow? That's where the Protection Profile (PP) comes in.
A PP is a set of standard security rules, checked and approved by experts, that you can follow for a range of products. Think of it as a trusted set of guidelines that ensures you're building your house right, no matter what kind of house it is.
The PP also has something called an Evaluation Assurance Level (EAL) or Substantial and High when EUCC is applied. This tells you how thoroughly the security has been checked and tested. The higher the level, the more rigorous the evaluation!

Security Target (ST) - Your Product's Customized Security Plan
Now, your house (product) might have some unique features. Maybe it has a special room or specific needs that the generic blueprint (PP) doesn't cover.
A Security Target (ST) is your customized security plan. It takes the general rules from the PP and tailors them specifically to your product. If your product fits into more than one category, you can use multiple PPs to create the perfect ST for you.
What We Offer
Securing Your Connected World: Tailored Services for Robust Cybersecurity

Preparation - Ready for Success
- Security Analysis: Understanding your product's environment, type, sensitivity of assets, and potential threats.
- Requirements Gathering: Understanding your specific needs, whether it's a consumer gadget or an industrial control system.
- Scope Definition: Outlining the extent of the security measures, ranging from the physical chip to cloud integration
- Regulatory Compliance: Ensuring that all necessary legal and industry standards are identified and considered.

Creation - Building with Precision
- Security Profile Development: Creating a tailored plan that encompasses your unique product characteristics.
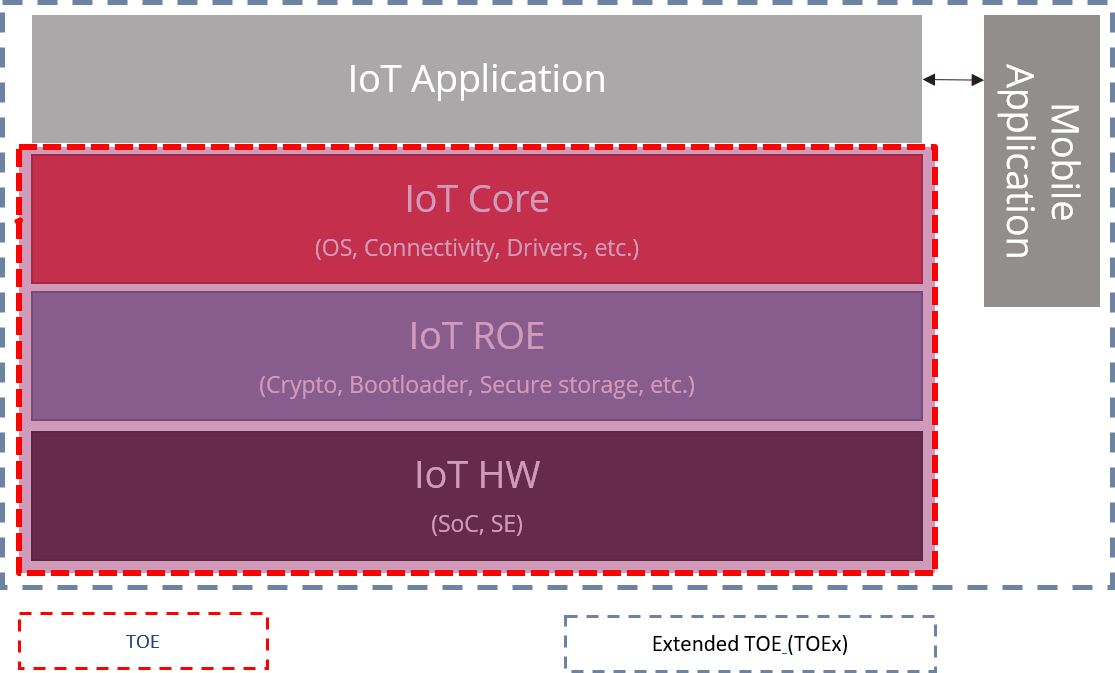
- Protection Profile Creation: From TOE definition to SFRs and SARs adapted them to the market specific needs.
- Security Target Crafting: Designing a custom security target that may combinesone or more PPs to meet your product's individual requirements.

Evaluation/Certification - Provide Trust
- Security Evaluation: Conducting rigorous testing and analysis to ensure the security consistency of the profiles with regards to an actual product and the rules defined in the applid standard.
- Certification Assistance: Guiding you through the Common Criteria (CC) or FITCEM certification process.
- Ongoing Support: Providing continued support to maintain and enhance security post-certification.
Potential Delivrables
💼 Preparation: Comprehensive Insight and Analysis
- Customized Needs Assessment: A detailed report outlining your specific requirements, providing a solid foundation for the creation phase.
- Risk Analysis Report: An exhaustive analysis of potential risks and threats, tailored to the operational environment of your product.
- Compliance Alignment Plan: A roadmap to ensure that your security approach aligns with all relevant regulations and industry standards.
📊 Creation: Tailored Security Documentation
- Security Profile: A synthetic document listing risk-based security requirements specific to your IoT product or solution.
- Protection Profile (PP): A standard, implementation-independent specification of security requirements, including threats, objectives, assumptions, functional requirements, assurance requirements, and rationales.
- Security Target (ST): A customized ST document that may comply with one or more PPs, providing a robust template for your product's security.
📚 Evaluation/Certification: Validation and Recognition
- Evaluation Report: A detailed report highlighting the findings of our rigorous security evaluation, including where applicable an analysis of how a typical product meets the specifications outlined in the ST and PP.
- Certification: Official certification according to the Common Criteria or FITCEM affirming that the product complies with the identified security requirements.
- Ongoing Support Plan: A framework for continuous support to help you keep up with evolving security standards and regulations.
Why Choose Red Alert Labs ?
Proven Expertise
Experienced professionals with a successful track record.
Economical Solution
Smart focus to spend effort where the risks are highest.
Standardized & Tailored Approach
Suitable for various industries and adaptable to specific needs.
Customer-Centric Collaboration
Personalized support throughout your security journey.
Talk to an Expert
Unlock True Security from Chip to Cloud and Elevate Your Security & Protection Profile Posture!
SIGN UP !
We'll reach out to you shortly !
Key Elements of security and protection profile
1Security assessment
We conduct a comprehensive assessment of your IoT systems' security posture, identifying potential vulnerabilities and developing a customized security plan to mitigate those risks.
2Threat modeling
We use industry-leading threat modeling techniques to identify potential security threats and develop effective mitigation strategies.
3Penetration testing
We conduct rigorous penetration testing to identify any weaknesses in your systems' security, helping you proactively identify and mitigate potential risks.
4Compliance and certification
We help you meet the highest standards of compliance and certification for IoT security, including standards such as ISO 27001, NIST, and others.
- Utilisez les sections de texte pour décrire vos valeurs, ou montrer plus d'information, ou résumer un theme ou raconter une histoire. Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt ut laoreet dolore.Utilisez les sections de texte pour décrire vos valeurs, ou montrer plus d'information, ou résumer un theme ou raconter une histoire. Lorem ipsum dolor sit amet, consectetuer adipiscing elit, sed diam nonummy nibh euismod tincidunt ut laoreet dolore.
EU Transparency Register: REG 450926493482-66
© 2024 Red Alert Labs. All rights reserved.